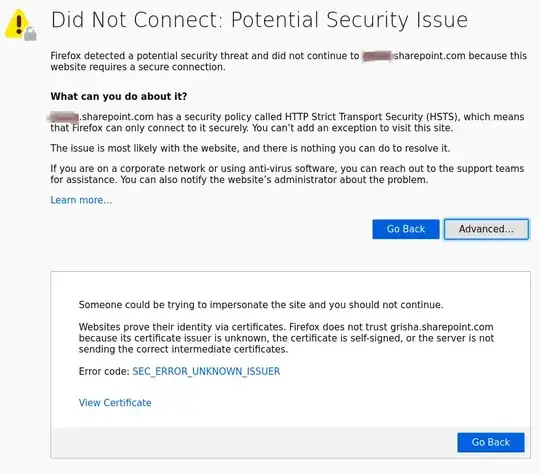
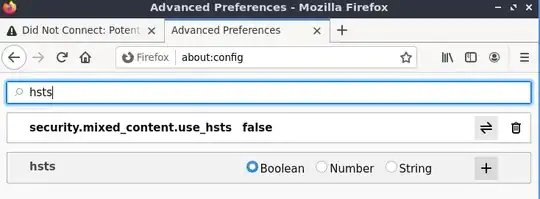
I want to investigate requests/responses between firefox and some private mysite.sharepoint.com site which I could access using my microsoft's email and password.
For this I've configured Burp Suite's Proxy (and Firefox Proxy settings) to
localhost:8085
Tried to configure on Certificates tab:
- Use a self-signed certificate
- Generate CA-signed per-host certificates
- Generate a CA-signed certificate with a specific hostname: myhostname.sharepoint.com
I could get two certificates using openssl s_client -connect grisha.sharepoint.com:443 -showcerts command:
CONNECTED(00000003)
depth=2 C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
verify return:1
depth=1 C = US, ST = Washington, L = Redmond, O = Microsoft Corporation, OU = Microsoft IT, CN = Microsoft IT TLS CA 4
verify return:1
depth=0 C = US, ST = WA, L = Redmond, O = Microsoft Corporation, OU = Microsoft Corporation, CN = *.sharepoint.com
verify return:1
---
Certificate chain
0 s:C = US, ST = WA, L = Redmond, O = Microsoft Corporation, OU = Microsoft Corporation, CN = *.sharepoint.com
i:C = US, ST = Washington, L = Redmond, O = Microsoft Corporation, OU = Microsoft IT, CN = Microsoft IT TLS CA 4
-----BEGIN CERTIFICATE-----
CERTIFICATE 1 CODE HERE
-----END CERTIFICATE-----
1 s:C = US, ST = Washington, L = Redmond, O = Microsoft Corporation, OU = Microsoft IT, CN = Microsoft IT TLS CA 4
i:C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
-----BEGIN CERTIFICATE-----
CERTIFICATE 2 CODE HERE
-----END CERTIFICATE-----
---
Server certificate
subject=C = US, ST = WA, L = Redmond, O = Microsoft Corporation, OU = Microsoft Corporation, CN = *.sharepoint.com
issuer=C = US, ST = Washington, L = Redmond, O = Microsoft Corporation, OU = Microsoft IT, CN = Microsoft IT TLS CA 4
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: ECDH, P-384, 384 bits
---
SSL handshake has read 4595 bytes and written 471 bytes
Verification: OK
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: SESSION ID HERE
Session-ID-ctx:
Master-Key: MY MASTER-KEY HERE
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 36000 (seconds)
TLS session ticket:
TLS SESSION TICKET HERE
Start Time: 1589794543
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: yes
---
Could I somehow tell Burp Suite to use correct certificates in case of access myhostname.sharepoint.com site
Adding hsts false option did not help:
Firefox version: 76.0.1
OS: Ubuntu 20.04