I am a beginner to TLS/Ops.
Our operations team have setup a number of virtual hosts with domains we own for hosting endpoints on our Cloud.
We have 3 virtual hosts-
- internal - to be used internally for integration purposes with the other departments in our organisation like Siebel CRM...
- partner - for organisations with which we do business.
- public - as the name suggests
All communication is over TLS.
There is a new partner to whom we(I am a developer) have exposed a new API.
When a developer from their team tries to consume our API with Postman, all he gets is -
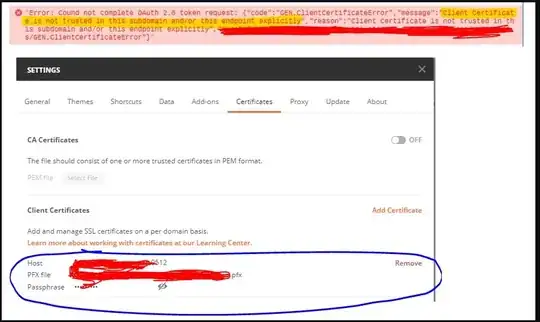
Client Certificate is not trusted in this subdomain and/or this endpoint explicitly
Their postman console shows this as seen in the attached image-
In the communication which our OPS team had with the client OPS team, I see that our Ops requested for a CSR file from the client and vice versa.
From the web, I see that a certificate signing request (CSR) is one of the first steps towards getting your own SSL Certificate.
Why would a client need our CSR file and similarly why would our Ops need theirs?