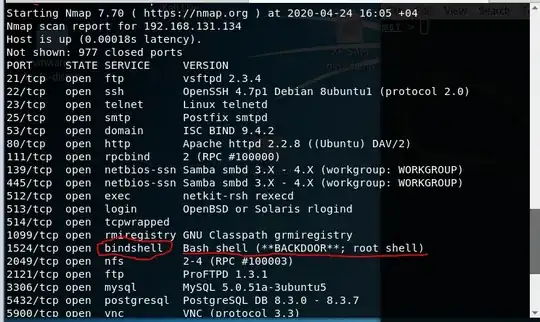
I just found out a bindshell backdoor, but I don't know how to access/connect to it using Metasploit.
I'm a beginner with exploiting; is there a way to access the backdoor? I tried to search for "bindshell" on Metasploit but I didn't find anything. I also searched "shell" and it displayed a bunch of reverse shell exploits. I don't know which one to use or if I used the right exploit.