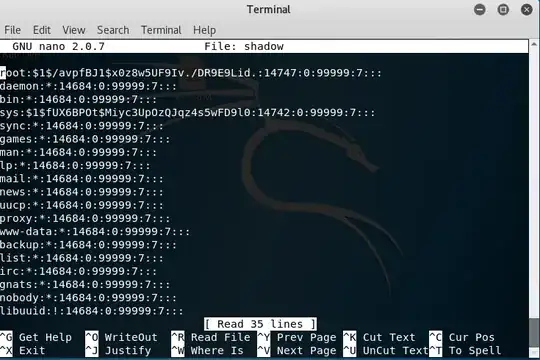
I've been struggling with encrypting this hash for a school homework. (Backstory) I had to gain access from my Kali Linux machine to an "unknown" Linux machine and I've done it, but now I have to basically get the username and password of the unknown Linux machine. I located the passwords file "/etc/shadow" and I nano'd the file to see the passwords and this came up:
The password that I need is for root, so I'm guessing it's this one?
root: $1$/avpfBJ1$x0z8w5UF9Iv./DR9E9Lid.
If you're able to decrypt it, can you please explain how you did it and what type of encryption it is?