I am attempting to encrypt some passwords by hand to use in a project with JtR. Unfortunately, the program is having difficulty recognizing the hash types of the passwords after hashing them.
Currently, based on the information found here: John the ripper does not crack password my process is to encrypt a password via openssl using AES-256, then piping the result into sha256sum on the command line
echo -n "password" | openssl enc -aes-256-cbc -a | sha256sum | cut -f 1 -d " " > hash.txt
The result for this being
I have also attempted piping the encrypted password directly into openssl's passwd function, although this has been less successful than the previous command
echo -n "password" | openssl enc -aes-256-cbc -a | openssl passwd -1 -salt xx > hash.txt
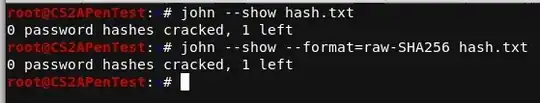
In any case, john does not seem to be able to recognize the hash format.
What exactly is happening here? It should be simple enough for JtR to recognize the encrypted hash, but obviously something is being mangled in the process. Is there an additional newline or other improper character being piped in along with the encrypted password? If someone could enlighten me it would be greatly appreciated.