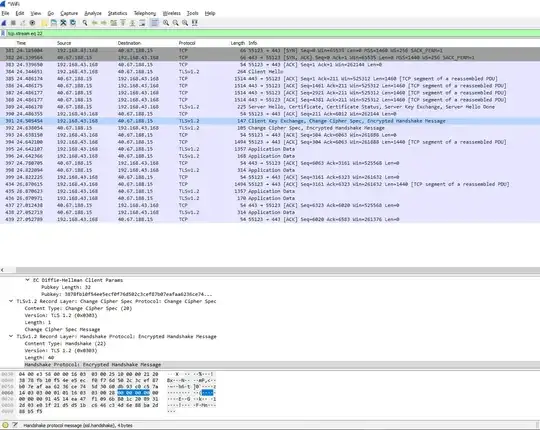
How can i decrypt Diffie-hellman TCP packets?
I'm trying to make a tool that shows cleartext response from a server that uses this encryption. However when i look online people all seem to say it's impossible to decrypt DHE, which is not true since we are the client and have access to this information,
but how can i decrypt these packets with the handshake in wireshark?
Bonus question: Any tools in python or something that establish DHE connections and show cleartext response?