I have been learning the famous "SIGNAL MESSAGING PROTOCOL",
Its brilliantly designed and perfectly secure , but I doubt on its implementations
Famous messenger services like Whatsapp and Signal claim to have implemented the e2e messaging protocol for message privacy , but where are the private keys (of users) stored?
I am pretty much sure that the private key isn't stored in the user's device because , I tired sending a few messages from device "A", switched it off, installed the same app in another device "B" and logged in with the same account. If the private key had been stored in device "A" then , I must not be able to read the messages from device "B" which I had sent through device "A" , but I was able to !!
So its pretty obvious that the private keys too are stored in the app's cloud.
If the messaging service provider too had access to the private key , then they could read any sorts of information transferred between me and the receiver through the app.
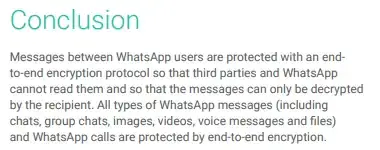
And whatsapp claims the following in their signal protocol implementation
Are their claims true?
Just Curious.. I am beginner, please correct me if my interpretation is wrong