I have a dedicated server with public IP address, opened port 22 and fail2ban running. I am using root account (I know it is wrong but I have to) and I have disabled logins with password. I am using an RSA 4096 bit key with key password (10 characters length with mixed letters, numbers and symbols).
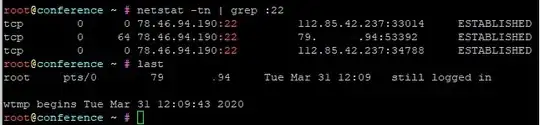
Today checking the server and some logs, I saw on the screenshot below 2 Chinese IP addresses and my IP address from my office (for privacy reasons I have blanked my IP address)
using last command seems to be the only one that has logged in at system.
Do I have to worry? Are there any tips to better secure my server? (running Ubuntu server Xenial 16.04 LTS)