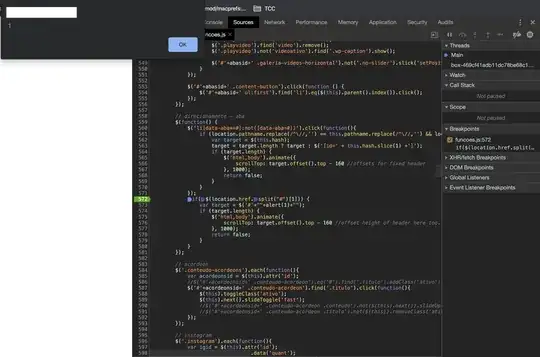
Target code:
if($(location.href.split("#")[1])) {
var target = $('#'+location.href.split("#")[1]);
if (target.length) {
$('html,body').animate({
scrollTop: target.offset().top - 160 //offset height of header here too.
}, 1000);
return false;
}
}
It uses from location.href, so I though about using an injection script like this:
target-url.com/#"+alert(1)+"", escaping the string and placing an alert(1) to trigger an alert in the page. If I edit the script using Chrome Dev tools, the script is successfully executed:
But when trying to inject this script in the URL, analyzing the browser console, I see a jQuery error:
jquery.js?ver=1.11.3:2 Uncaught Error: Syntax error, unrecognized expression: %22+alert(1)+%22%22.
It appears to fail because it's replacing " with %22. But I need to scape the string scope, since location.href.split("#")[1] returns a string, and I need to leave the string scope to run the script.
Is there a way to bypass this URL encoding or this scenario is not exploitable at all?