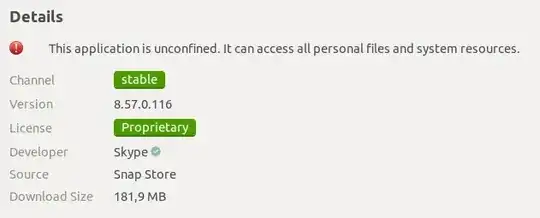
Why am I getting this message?
The idea of snap is to be an "app store for Linux", with much of the same benefits as app stores for other platforms, such as iOS or Android. One of the big advantages is that applications are rather confined, unable to interact with your OS unless the user gives it specific permissions.
In snap, there are several different "confinement" settings, as documented here:
Strict
Used by the majority of snaps. Strictly confined snaps run in complete isolation, up to a minimal access level that’s deemed always safe. Consequently, strictly confined snaps can not access your files, network, processes or any other system resource without requesting specific access via an interface (see below).
Classic
Allows access to your system’s resources in much the same way traditional packages do. To safeguard against abuse, publishing a classic snap requires manual approval, and installation requires the --classic command line argument.
Devmode
A special mode for snap creators and developers. A devmode snap runs as a strictly confined snap with full access to system resources, and produces debug output to identify unspecified interfaces. Installation requires the --devmode command line argument. Devmode snaps cannot be released to the stable channel, do not appear in search results, and do not automatically refresh.
The Skype app is most likely a "Classic" snap, which means you don't get the same benefits as from a strict confinement.
Can Skype really do anything on my system?
Skype can do as much as any other traditional binary can do, such as those installed via apt. It does not generally become "some kind of super user", but it could use sudo or other means to ask to become a privileged process. The easiest way to do that is to simply refuse running as anything but root.
However, Skype cannot magically bypass any file permissions, unless you specifically gave the binary capabilities to do so.
What does it mean by system resources?
Think about apps on your smartphone. Applications have to ask to access your files, your contacts, your microphone, your camera, your location, etc.
Snap in its strict confinement setting does allow applications to access these, but individual applications need to request access to these interfaces. Of course, you as the user can forbid an application from accessing them. Perhaps you don't want an application to access the network because you don't want to use network-enabled features.
What the installer is telling you is that, since Skype is a "classic" snap, you cannot stop Skype from accessing all these resources (network, camera, etc.), at least not in an easy way.
How is it possible to confine such an application?
You can, if you so desire, try to create a strictly confined snap yourself. I assume that this will be a difficult-if-not-impossible task, else Microsoft had done that. Or maybe it's super easy, barely an inconvenience, and Microsoft just didn't care.
You could also create a limited user and configure your system to run the application as this user, then restrict that limited user from accessing resources such as the network, the web cam, etc.