Protecting memory from the host is going to be the tricky part.
Testing
My Setup
To demonstrate this, I have this system lying around:
- Host: Ubuntu 18.04.4 LTS
- Virtualization stack: VirtualBox 5.2.34
- Guest: Kali linux 2018.3
Experiment
In Kali, I opened a text editor and typed the text "SecretForcn271828n", but I did not save it to disk, it's just in memory. The test is whether I can read that from the host.
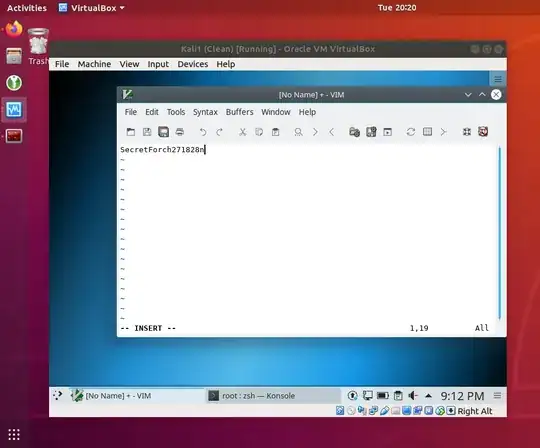
Steps
From the host, the entire VM appears as a single process:
➜ ~ ps -aux | grep Kali1
mike 6014 12.2 23.6 4524784 1901772 ? Sl 19:48 3:26 /usr/lib/virtualbox/VirtualBox --comment Kali1 --startvm 7b229c8a-ba68-48ad-bd80-0ab5ed9b6b86 --no-startvm-errormsgbox
So I'll take a core dump of that process:
➜ ~ sudo gcore 6014
...
Saved corefile core.6014
➜ ~ ll -h core.6014
-rw-r--r-- 1 root root 2.3G Mar 3 20:02 core.6014
That core file contains a complete dump of the memory of the kali OS, plus whatever memory the VirtualBox stack itself is using, as seen by the root user on the host.
Now let's use the strings utility to see what's in memory!
➜ ~ strings core.6014 | grep -i secret
ccSecretForch271828n
SecretForch271828n
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
-- INSERT -- 1,19 All
SecretForch271828n
That certainly looks to me like the host can see the raw memory of the gvim application that is running inside the kali VM.
(this was actually all on one grep line, but I formatted it pretty)
Summary
Trying to protect a guest VM from the host is a losing game. Anything that is in raw memory within the guest will be visible to the host. The CPU instructions executed by the guest are likely similarly visible, but it's beyond my skill to demo that.
It might be possible to build a guest OS, or maybe a hypervisor or virtualization stack, that adds some memory obfuscation (such as encryption of live memory). This would come at a pretty steep performance hit, and at best it would be obfuscation because, with enough effort, and attacker who controlled the host could find the encryption key in memory of the guest OS or virtualization stack.
