There is a web server I'd like to recon using httprint.
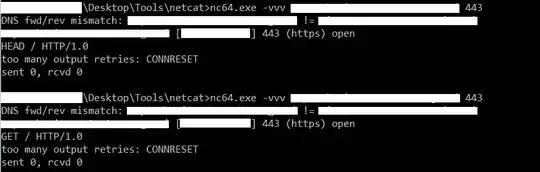
But that web server has a basic auth protection on 443. Port 80 is not responding.
When I launch httprint, it says Unspecified Error
The same thing happens with netcat. It fails because of Basic Auth (ie "Connection Refused") When basic auth is disabled, both netcat and httprint work well.
How can I bypass basic auth for fingerprinting a web server?
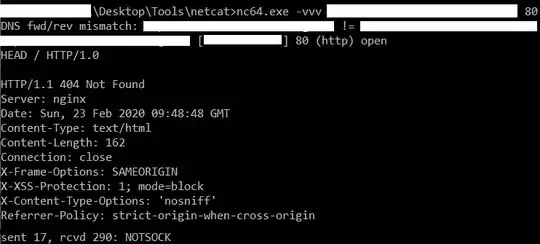
I believe netcat works below for 2 reasons 1. There is no basic auth on the port 80 (it's a different web app showing on port 80) 2. There some sort of load balancing or reverse proxy because the app on port 80 is different of the app on port 443 although both have the same IP address