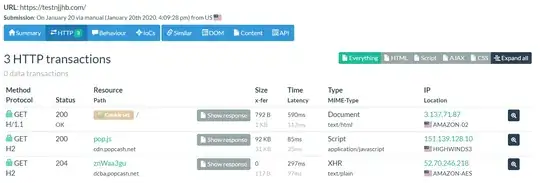
On the last few days, one of our endpoints calls to testgvbgjbhjb.com the calls came from google chrome outside.
I used TCPView to find suspicious connections and check if there any unknown extension.
The owner of the domain made it a 127.0.0.1 record and set the next txt record:
"The owner of this domain does not know why your machine is reaching out to it. Owner saw suspicious traffic in multiple networks and bought it."
I read the next analysis but I can't find the cause of these calls.
Any Idea?