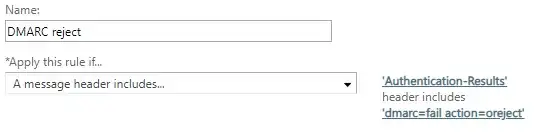
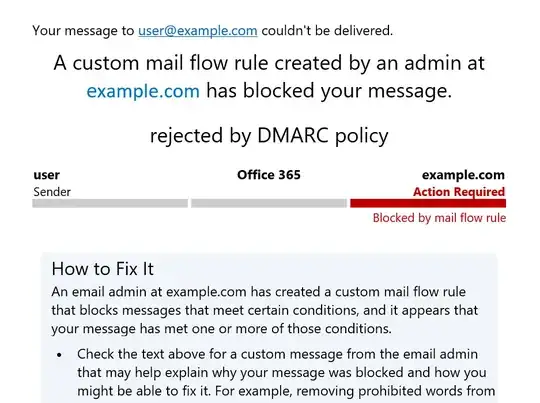
The domain & tenant has SPF and DKIM properly configured and DMARC policy set to p=reject. Still, emails spoofed with the domain in the From header aren't rejected, but appear in the Junk Email folder on Office 365. People do check their Junk Email for false positives, and are still reading all the CEO frauds, sextortion letters etc.
This seems a feature instead of a bug, as described in Microsoft's documentation:
How Office 365 handles inbound email that fails DMARC
If the DMARC policy of the sending server is
p=reject, EOP marks the message as spam instead of rejecting it. In other words, for inbound email, Office 365 treatsp=rejectandp=quarantinethe same way.Office 365 is configured like this because some legitimate email may fail DMARC. For example, a message might fail DMARC if it is sent to a mailing list that then relays the message to all list participants. If Office 365 rejected these messages, people could lose legitimate email and have no way to retrieve it. Instead, these messages will still fail DMARC but they will be marked as spam and not rejected.
However, this reasoning has some flaws:
DKIM protects legitimate mail; DKIM signed messages do pass with the DMARC policy even if it fails to align with the SPF when forwarded on a mailing list. (Mailing lists should change the envelope sender to pass SPF checks, anyway, so the SPF checks are probably passed, but not aligned.)
By implementing
p=rejectinstead ofp=quarantinethe owner of the domain has stated that the emails should be rejected. Therefore, Microsoft's implementation is against RFC 7489, 6.3:p: Requested Mail Receiver policy ...
reject: The Domain Owner wishes for Mail Receivers to reject email that fails the DMARC mechanism check. Rejection SHOULD occur during the SMTP transaction.
Is there any setting on Office 365 to alter this behaviour and reject these messages?