Right now I'm looking at an office document (most likely rtf based on it exploiting equation editor) that opens just fine when you double click it, but on further examination in a hex editor and in entropy analysis (7.9) is technically encrypted, even without requiring a password to open. It seems as thought the workbook is protected, and I'm not sure how to access the cleartext version of the document on disk.
I need to know which vulnerability the document targets to determine coverage, but I don't know how to remove it.
How do I remove the "protection" from the workbook so I can save it without knowing the password? Trying password crackers "works" (I can still open the file and view it) but it seems to corrupt the file such that I can't save it as cleartext to examine it's internals.
I should mention that this is an .xlsx file.
Additional details based on conversation in meta:
Technical details:
- The file format is MS Compound (0xd0cf11e0 magic)
- The file pops it's exploit without enabling macros even though it has the standard social engineering image telling you to do so.
Things I've tried:
- Olevba: no macros
- The rest of oletools: either return nothing or return the same thing as using 7zip
- office2john.py -> johntheripper: password is not in the dictonary and 2.5 hours on 8 cores does nothing.
- I remember running the script on this site: http://www.excelsupersite.com/how-to-unprotect-an-excel-spreadsheet-if-you-have-lost-your-password/ and it not working, but trying again it prevents me from opening the dev console and I don't remember what I did to make it work the first time.
- I know I did something else, but I can't find the source for it again, and looking for the anchor phrase in the hex turns up nothing, so I must have done something else to the file last time that I can't remember doing. For the sake of being thorough, lets assume I didn't try anything with editing the hex of files or running the VBA script since I can't remember how I got it to work the first time.
My thoughts / needs for the file:
- The file can be opened without the password, and the exploit works and beacons without the password being manually input, so the file obviously gets decrypted based on the key being either in the file itself or office knowing a key to decrypt, otherwise you wouldn't be able to load the file without knowing the "secret". Even olevba can get into the file so I know there are shortcuts that don't involve knowing the original password
- I don't need to know the original password used by the actor, I don't even need a working office document when I'm done, I just want to dump the decrypted internals so I can run yara against them to determine whether we're patched against the vulnerability.
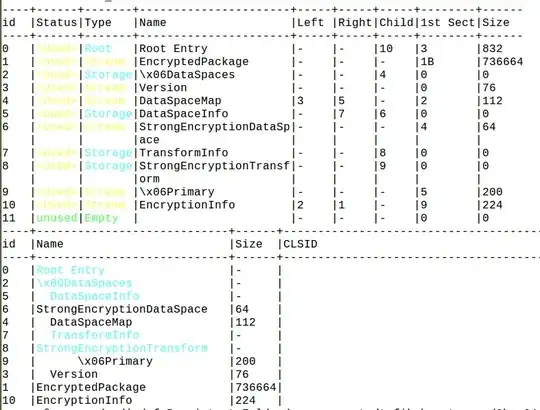
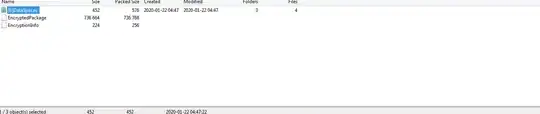
This is what shows up when I open the file with 7zip
Also, I feel stupid for not having done this before, but the file is in VT so I can actually share it here: https://www.virustotal.com/gui/file/18022f77bea3783582df27ebf9b6d1eb8067e245d114498f3ba6b27a0044e45d/details
I know that VT lists the exploit directly in the header, but I need to know how to do this myself in case the next one isn't in the public domain and I can't submit it to VT (if the file is targeted then I can't share/post it on public platforms for opsec reasons).