UPDATE:
Looking at the product again, I don't think this even has built in Wi-Fi (it uses bluetooth for the connection).
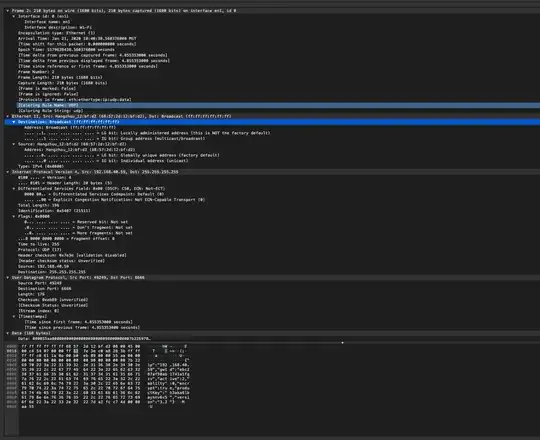
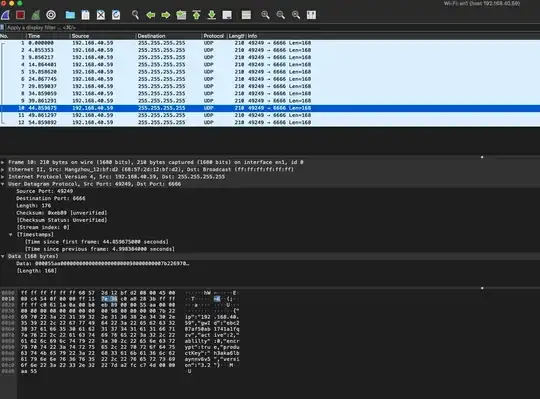
I don't know what I am looking for here in Wireshark, but I added the host 192.168.40.59 and ran it for about 15 seconds and there was a constant packet that was captured, maybe a ping?
I was going through my connected client list trying to add some alias names to my devices to help keep track of what is connected to my network.
I noticed one device that I didn't have a name for, and had trouble trying to track down what it was.
Checked the MAC address to try and find the vendor and got some basic details, enough to recall what this was.
I have a "Smart Wifi Lightbulb" which comes with an app to change its colors etc.
When I ran NMAP on the IP, it said that service=IRC was running on port 6668. I know that there are only a limited number of ports so there are bound to be devices that share ports that might not be what they are actually for.
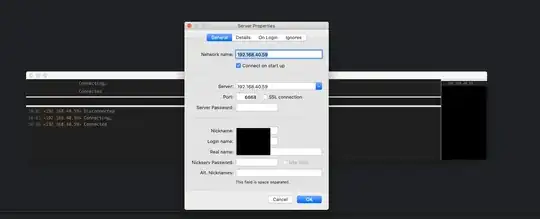
As a test, I pulled up an IRC client and put in the IP and the PORT and it connected. It stays open for about 30 seconds and then disconnects.
Anything I should be worried about here or further things I should check into?
Product: https://www.amazon.com/gp/product/B07CL2RMR7/
MAC: 68:57:2d:12:bf:d2
Vendor: HANGZHOU AIXIANGJI TECHNOLOGY CO., LTD
Main Products: Smart LED Light Bulb, Smart Plug, Smart Switch, Smart Module
Mac-mini:~ $ sudo nmap -sS 192.168.40.59
Password:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-21 10:01 MST
Nmap scan report for 192.168.40.59
Host is up (0.076s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
6668/tcp open irc
Nmap done: 1 IP address (1 host up) scanned in 1.12 seconds][1]][1]