For the sole purpose of learning, I am trying to figure out how disk encryption software is able to recover password of an encrypted disk using a challenge response mechanism.
Th recovery process usually goes like that:
- You forgot your password on a device that has an encrypted disk (eg : laptop). The PBA (pre boot authentification) will generate a challenge (eg:
32 alpha-numeric characters, which AFAIK is approximately 160 bits of information). EDIT: 32 hexadecimal characters, which is exactly 128 bits (as reported by fgrieu in comments). - You communicate that challenge to a third party (eg : IT department), along with some info that identify the device. They generate a response.
- You enter the response in the PBA. This allow you to generate a new password and decrypt the disk (and thus to boot the system again).
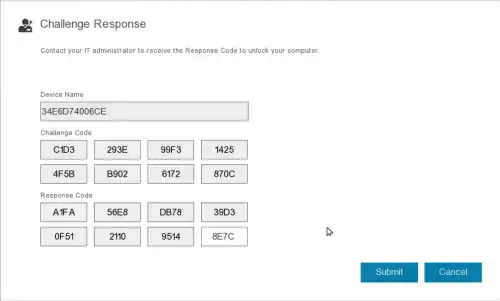
Here is an example :
AFAIK the response is too short to be the master key itself (the key which encrypt the whole disk). This would also be insecure.
How I think it works (I might be wrong on this) :
The encrypted disk store the master key twice. Once encrypted with user password (which is now lost) and a second time using another password that only the third party (eg : IT department) know. The challenge-response exchange allow to decrypt that masterkey (and thus decrypt the whole disk).
I am aware there is probably lot of different implementations used by disk encryption software so a single, exact answer is not possible. I would like to know one possible way to implement this recovery mechanism in a secure way.