After seeing multiple answers with mixed conclusions here and in Google searches, as well as no thorough explanations on whether or not Windows 7 is effected by this vulnerability, I took it upon myself to determine the true answer and show my testing process.
Below are screenshots of a fresh Windows 10 installation in a Virtual Machine(VM) within which I use a website (https://curveballtest.com/) that has Proof-Of-Concepts(PoC) available for this vulnerability, this is a control to prove this is working.
Windows 10
Information about the Windows 10 installation.
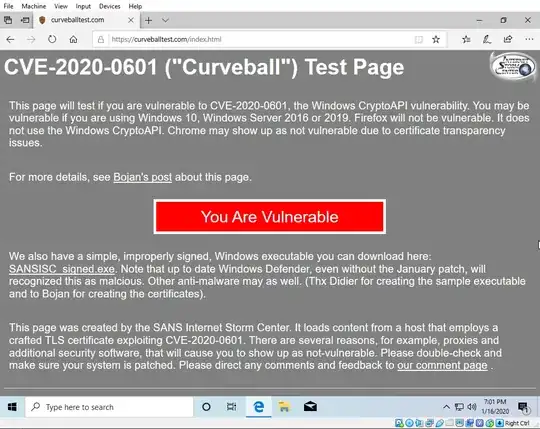
Showing the https://curveballtest.com/ PoC for spoofing certificates for HTTPS working on the Windows 10 installation.
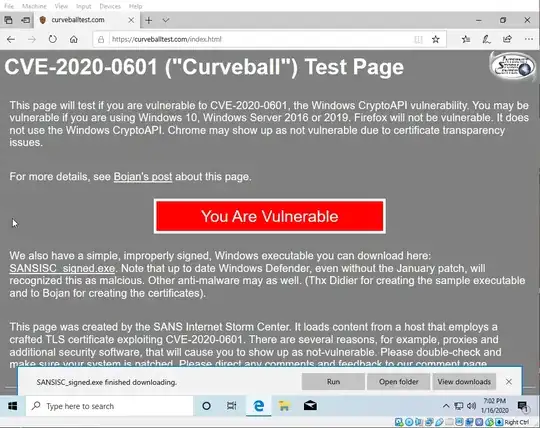
Showing the https://curveballtest.com/ PoC for spoofing signing for an executable working on the Windows 10 installation.
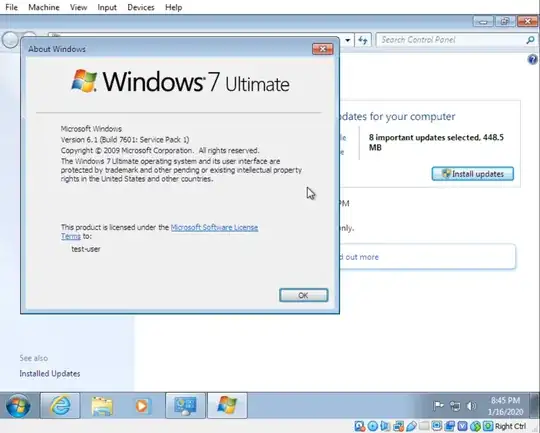
Now I have also created a fresh Windows 7 installation in a VM, below are the results for the https://curveballtest.com/ PoCs.
Windows 7
Information about the Windows 7 installation.
Showing the https://curveballtest.com/ PoC for spoofing certificates for HTTPS NOT working on the Windows 7 installation.
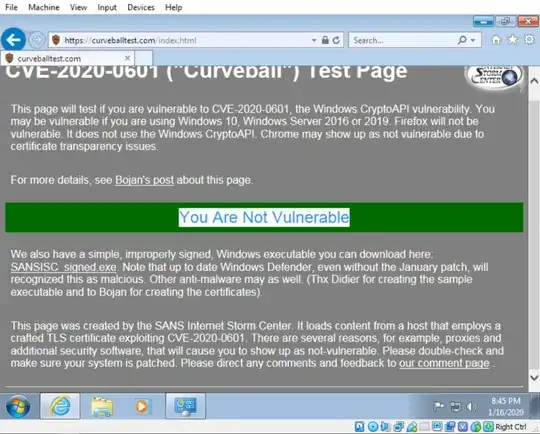
Showing the https://curveballtest.com/ PoC for spoofing signing for an executable NOT working on the Windows 7 installation.
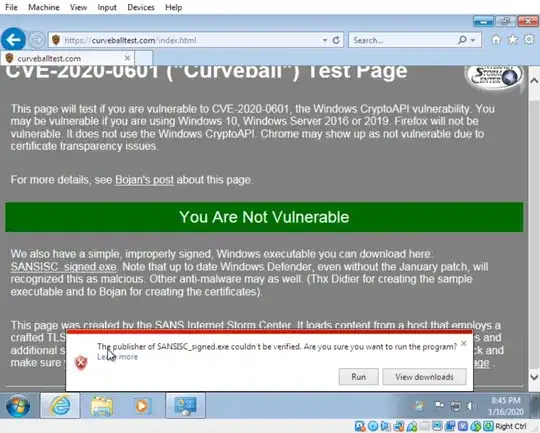
From this testing, we can effectively conclude that Windows 7 is NOT vulnerable to CVE-2020-0601.





