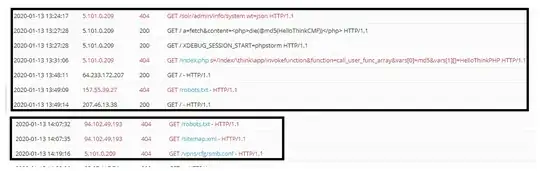
I was doing my plesk hosting logs checking for web and database development. Somehow, I had seen some weird ip trying to communicate to hosting. Wonder what is the purpose of these anonymous requests. Should I just ignore them as they are common issue happening around?
Thanks in advance. P/S: This website still in development stage, should be no one knowing this website address.