I recently found out that in order to log on to the web-based administration tool on my ISP-provided router, I need to accept a self-signed certificate it offers. I did a bit of reading and it sounds like self-signed certificates issued by an ISP can enable the ISP to perform MITM attacks on computers that accepted the certificate. (see Is it common practice for companies to MITM HTTPS traffic?)
Is this something I should be concerned about in my situation? If I accept the certificate, will I potentially be compromising end-to-end encryption with parties other than the ISP or my router's software?
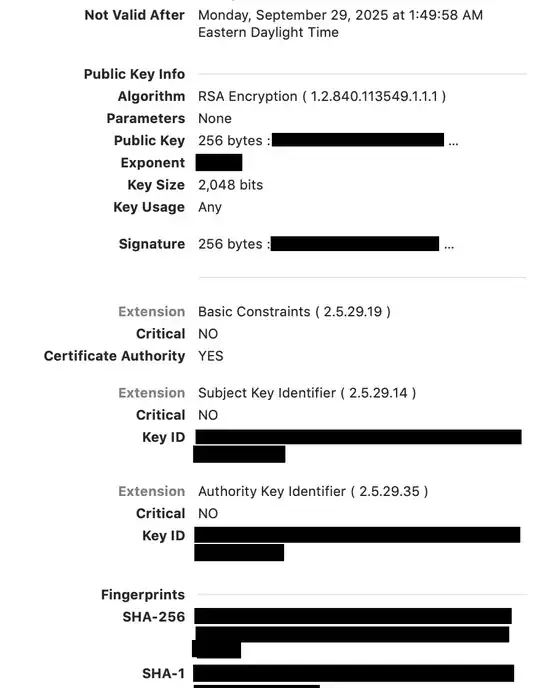
When I view the details of the certificate, it says "Root certificate authority". Is this a synonym for self-signing or can this certificate be used for a MITM attack?
Here are screenshots of the details of the certificate, with things that looked like I shouldn't spread around on the internet blacked out: