In my project I have to integrate with another system which uses quite specific SSL (and also specific cipher suite). Here's what I mean.
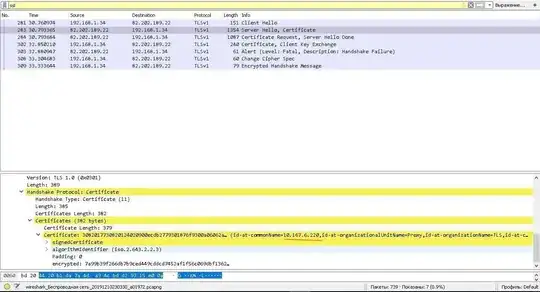
Whenever I try to access the server with Java (send a request), I get the wrong certificate from Server Hello. Subsequently, I get a handshake failure, even though I have installed root and lk.egrz.ru certificates in java's cacerts
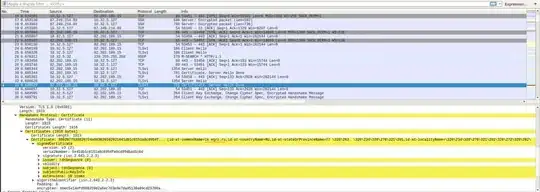
However, if I try to access the same server but with a browser with installed server certificates on Windows machine (root and lk.egrz.ru), I get the right one and a handshake succeeds:
My question is whether it's possible to have such SSL which can deliberately send a wrong certificate if client is accessing the resource not with a browser, but with an agent.
I have no idea why in some case I'm presented with a wrong certificate and in another case with the right one.
Thanks in advance