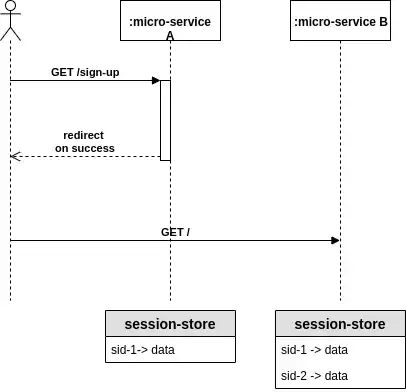
I am evaluating the above service design where I want to have mechanism to pass a user through multiple microservices. In this simple example, the user goes through a sign-up process and once done, the user is redirected to another microservice (B).
The session-id for microservice A is stored in a session store. However, when the user is redirected to microservice B then a new session-id is generated by microservice B and so this is stored as well in the session store.
This allows the user to traverse back and forth between microservices. Are there any security implications with this design?