summary
If you decap the dies, you can. The pads exist but are not bonded but available. The reason that you can get the information is that the timers that are used to inject and tunnel the floating gates do not push the data hard against the voltage rails. If the hardware supported a "tunneling on forever" type of control word, you could make it so that data extraction is more difficult.
short answer
I happen to have an IC from a commercially available 14nm SOI, FinFET process from 2012 that had a NOR FLASH bank which I know made it into prime-time. These ICs were development ICs before the process goes prime-time, and I used this process to make asynchronous FPGAs. This device has an array of the 64KiB "pages", where each page had a timer that is used to tunnel the device, which makes the floating-node go positive, and injection through a nFET to make the node go negative. Please see my link on analog floating gates, as it is similar to digital FLASH. The only difference is that there's thresholding to be a "1" or a "0" on the readout circuitry.
I will write this from the reference of the floating gate device. The nodes are made negative by the high field across the nFET. The details of this are in chapter 2 of Jennifer Hasler's dissertation under Carver Mead. I did not go into FN tunneling details in the analog floating gate post. If you read into the boundary conditions, as you make a node more positive or negative, the injection or tunneling efficiency become lower. Due to the fact that the injection and tunnel are controlled by timers, a "1" or "0" is not really a "1" or "0" that corresponds to a "VDD" or a "GND", but some voltage that is adequate to be sure you are positive or negative enough. On this process, the digital voltage is 800mV, and a voltage below 300mV would be the "off" state, and above 600mV would be the "on" state. To understand why this is, you need to consider the physics, but fundamentally, it's easier to tunnel a transistor than inject it.
Here's what tunneling looks like (this is the short, short version)
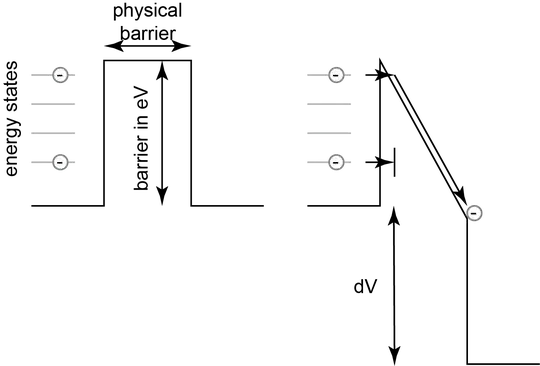
If you have a barrier, and you make it electrically thin enough, there is a probability that the electron will be able to penetrate the barrier. This is "tunneling", and it's as a ball through a wall, and it's a quantum effect In the two images, I give a zero voltage difference, where the barrier symmetric. The SiO2 barrier is 9.2eV in this process, and the oxide thickness of the floating-gate is 180angstrom (I measured this). As you change the voltage between the floating-node and the tunneling junction, you pull electrons off the node with the higher potential. In the image, the electrons at higher states will fall off first. You can just consider it a pile of electrons. One of the issues is that you need more voltage to take off more electrons and the node becomes more positive. As an example, if the node is set to be 1V, and I tunnel at 11V, there's a 10V difference. If I pull off enough charge for to have 2V on the floating-node, you have a 9V difference, and the barrier is less thin and it takes longer to tunnel.
Now to the crux of it, and I can elaborate if someone wants me to. The caps seem to be 2fF in depletion, which means that's their maximum capacitance, by my measurement. This means that there's 1248 electrons per volt. Due to the debugging frame, I can set the gate voltage and measure the current through the drain of the fg-nFETs, and the lowest that I can see is 20fA. 100 electrons changes the gate voltage by 80mV which is about 1 decade of current in subthreshold (diffusion current). I found that by writing 0x5A, for a b'01011010, I could always read back a current that indicated the last state. This is due to the fact that the injection/tunneling control circuits are designed to be fast. There's not a way for me to tunnel without a write, due to how the system is set up, and even if I made the nodes positive, I could always read out the previous states.
For this reason, I would say that an aggressive actor would be able to extract FLASH data. You need a semiconductor test lab, and access to the test pads, but there's nothing to stop you. My recommendation would be to have a control word to tunnel the nFETs for a long time to make the nodes as positive as possible, because they'd eventually all settle at the same voltage. Also, they will be in drift (above threshold) transport, and it would be more difficult to determine the previous state, and the differences will fall into noise.
