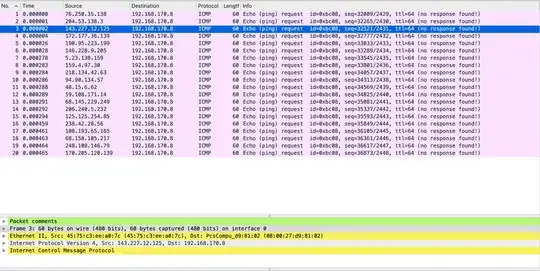
There is supposed to be abnormal behaviour here, and I see that there is. But I can't figure out what it is.
There is no response from the ICMP requests. Furthermore some packets have the warning:
[Expert Info (Warning/Protocol): Source MAC must not be a group address: IEEE 802.3-2002, Section 3.2.3(b)] [Source MAC must not be a group address: IEEE 802.3-2002, Section 3.2.3(b)] [Severity level: Warning] [Group: Protocol]
I was thinking it might be a Ping flood attack, but shouldn't there also be a reply/response from the destination address for this to be the case? The host might already be overwhelmed thus making it unable to respond to the ICMP requests, but that isn't shown in the capture file.
The packet length is 60, so it doesn't match it being a Ping of Death attack either.
Any help is greatly appreciated!