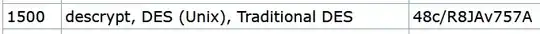
I want use hashcat or John the Ripper to crack the hash of a password. I know the password was created using the following command:
openssl passwd -crypt -salt tl ********
The asterisks, of course, are placeholders for the actual password. I know for sure that the password has 8 characters, and that the salt is tl. How exactly can I use hashcat or John the Ripper to crack the password hash?