Is this a standard part of vulnerability scanning as far as PCI is concerned?
No, it's unusual, and having worked with 4-5 different auditors, I've never been asked for that.
It's much more common for the auditor to request certain evidence - either the auditor 'rides shotgun' while you gather the evidence, or they trust you to gather the evidence - from a statistically significant sample of hosts.
First of all, there's the responsibility issue. If you give them admin credentials, and then they do anything wrong while poking around with your servers, and cause downtime or damage, that's a big problem. A good auditor will be even more interested in avoiding that than you are!
But secondly, and more importantly, let's see what SAQ A-EP is asking them to do:
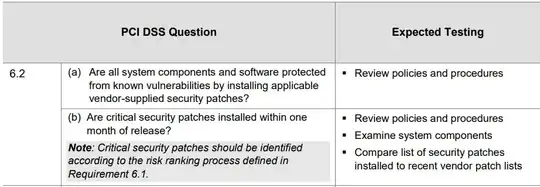
For patching, the expected testing is to "Review policies and procedures". For critical patches it adds "Examine system components" and "Compare list of security patches installed to recent vendor patch lists". In my experience these have always been satisfied by providing the installed patch list to the auditor. The more stringent auditors I've dealt with required me to gather that evidence in front of them to prove its provenance.
I have had auditors who asked me to run an information gathering script on a sample of hosts - which we did, after examining the script, and running it on non-production hosts first to make sure it didn't cause problems. But, again, they had no interest in running it themselves, and didn't ask for any access to the servers.
