Concept of Rings
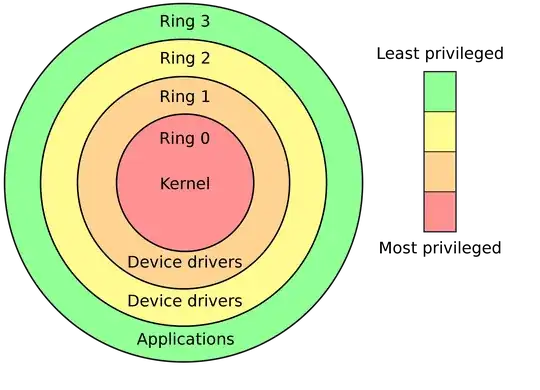 Rings were introduced in the forerunner of UNIX, Multics, and had 8 rings for reading, writing, executing and calling (I don't quite understand why it needed 8 rings to do this, if anybody does consider that a bonus question!). The x86 architecture by Intel incorporated the idea of rings into hardware, with 4 rings corresponding to ring 0 being for the kernel, 1 and 2 for device drivers, and 3 for applications.
Rings were introduced in the forerunner of UNIX, Multics, and had 8 rings for reading, writing, executing and calling (I don't quite understand why it needed 8 rings to do this, if anybody does consider that a bonus question!). The x86 architecture by Intel incorporated the idea of rings into hardware, with 4 rings corresponding to ring 0 being for the kernel, 1 and 2 for device drivers, and 3 for applications.
Situation in 2019
Ring 0 and 3 are typically the only ones used in modern x86 operating systems for most users, with ring 0 being reserved for kernel-level operations and ring 3 for user-level, although there are some exceptions; for example, VirtualBox uses ring 1 to allow the use of virtual hosts. Generally, code in ring 3 can't access memory or operations in ring 0, although that was at the root of issues from Spectre and Meltdown disclosed in January 2018.
'Ring -1' has also been introduced for hypervisors - Intel VT-X and AMD-V add 9 machine code instructions, introducing the concept of ring -1. Ring -2 is typically called SMM (system management mode) and is used for very low level operations such as power management and used only by system firmware. It has been used with multiple exploits for rootkits to reside in without the operating system being able to interefere.
'Ring -3' was coined for levels operating below that after an attack was demonstrated by Invisible Things on the Intel Q35 chipset (fixed in Q45 and later). This worked by remapping the first 16 MB of RAM reserved for the Intel Management Engine and operated even with a device in an S3 state.
ARM processors seem to use only 3 rings, ordered the other way around; PL0 being user, PL1 being operating system, PL2 being hypervisor. See Figure 3.20 and this page from ARM.
Summary and question
There have been several exploits over the years demonstrating exploits on rings outside those originally described by the x86 architecture. What would an even lower-level ring look like (ring -4 in Intel, PL3 in ARM, or ring -3 in AMD) and has there has been any work regarding exploits in this area. Additionally, I've tried to follow the guide on good suggestive questions so that explanations on the 'how' and 'why' are applicable.