I have a Raspberry Pi connected to my network and keep getting this vulnerability warning from my security software. I turned off the apache2 web server on the Pi, which fixed my port 80 issue but have no idea how to fix the remaining port issues (8080 and 8443 below). I need to fix these vulnerabilities without removing my SSH access. Is this easily fixed by adjusting permissions to files or do I need to do something else? My webpage code is written in HTML and PHP if that helps. The webpage is shutdown after it accomplishes its purpose but I am still vulnerable to traversal. How do I fix this? Thanks in advance.
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxy
| http-passwd: Directory traversal found.
| Payload: "/../../../../../../../etc/passwd"
| Printing first 250 bytes:
8443/tcp open https-alt
| http-passwd: Directory traversal found.
| Payload: "/../../../../../../../etc/passwd"
| Printing first 250 bytes:
sudo netstat -lptu results are:
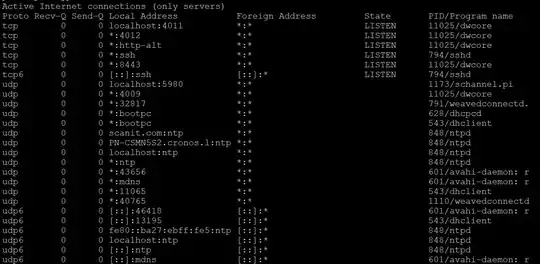
NOTE: "dwcore" is deviceWISE M2M by Telit just adding some more info in case that helps
- TO REMOVE "dwcore"
sudo /opt/dw/devicewise stop
sudo /bin/sh/etc/software/dwgateway_raspbian.remove
sudo rm -rf /opt/dw