tl;dr
No, this completely falls within the realms of fiction!
The longer explanation
For something like this to work, Alice would need to find an exploit in the camera of Bob, which would then prevent Bob from taking a picture. The only ways of Alice to exploit Bob's camera is for her to send some kind of information to it.
Possible ways for her to do this would either be via what the camera "sees" or via some other channel (Bluetooth, Ad-Hoc Wi-Fi, etc.).
The first way is, to be frank, absolutely nuts. There are exploits related to images and specific image formats, but all those exploit the specifications of how image files are read, rather than the pixels on it.
As far as Bluetooth or Wi-Fi goes, this is a little bit more believable, but just barely above "Zoom and Enhance". If Alice could connect to Bob's phone via Bluetooth, there may be an exploit she could use that would disable the camera app.
However, if Bob used a dedicated camera instead of his phone, then Alice is out of luck and her picture will be taken.
How could I protect myself from having my picture taken?
There are, however, creative ways to hide yourself from cameras. After all, reality can be so much cooler than fiction if you get a bit creative.
Infrared LEDs emit infrared light. This light is not visible to our eyes, but to cameras. This difference is something that hackers can exploit.
By attaching many, high-powered infrared LEDs to your clothing in a way that they shine on your face (e.g. through LED strips on the inside of your hoodie, on your baseball cap, etc.), your face will receive much more light than the surroundings, causing your face to be extremely overexposed.
This will probably stop security cameras, since they will try to set their exposure in a way that most of the picture (i.e. your surroundings) are illuminated correctly.
Somebody taking pictures manually of you may be able to set the exposure correctly, showing your face, but making the rest of the picture very dark. With some clever image manipulation tricks, and multiple pictures taken at different exposure levels, you can be shown in your surroundings, even with such LEDs in place.
Cool, can I see how that looks like?
Here you can see a picture of glasses with just a few LEDs:
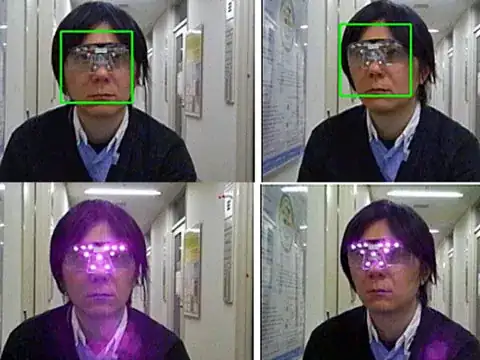
Attribution: Tokyo National Institute of Informatics
The two pictures on the top are with the LEDs turned off. This is how a person would see it. The green frame shows that a camera has detected a face.
The two pictures down below show the LEDs turned on. It's much harder to detect details of the person, but it's still doable, especially if you have some reference image. The camera, in this case, failed to identify a person.
With more and/or stronger LEDs, the effect will be much stronger.
Here is also a video, showing them in action with a typical webcam. Again, with some reference, a person is still identifiable.
What about the downsides to this?
Before you go online and order a 500 pack of infrared LED strips, there are some downsides to this technique.
- A battery or some other power source is required. This may be the least of your worries, since LEDs don't draw that much power, but running around with a 9v in your pocket may become annoying.
- You don't see if it's not working. Unless you regularly take selfies of your overexposed face, you don't know if your security system has failed.
- Since you quite literally look like a shining ball of light on pictures, people reviewing security camera footage will probably start investigating why Jesus is casually walking through the mall. It does attract unwanted attention, is what I am trying to say.
- You depend on your clothing. Depending on where you go, it might not be feasible to wear clothing close to your face, such as a swimming pool. You may be able to wear a baseball cap, but then you run into the problem of a power source.
