I'm using BurpSuite to intercept the HTTP/HTTPS requests sent when logging in on https://www.nike.com/. I'm trying to achieve this with the following step:
Opening BurpSuite and Firefox
Turning on the proxy intercept
Turning on FoxyProxy on Firefox
Opening the website and trying to logging
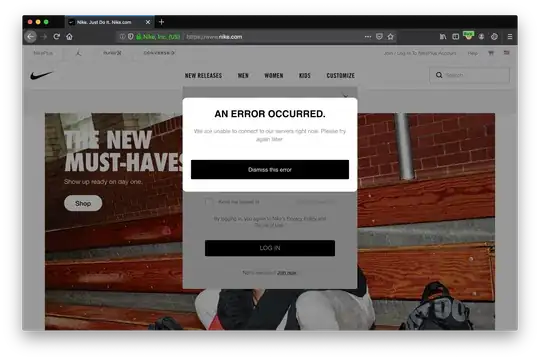
These steps usually work for me, but in this case, I'm getting a "we are unable to connect to our servers" error without anything appearing on the intercept tab when trying to logging (I have tried turning off the intercept feature but it still yields the same issue, so I think it might be a proxy and certificate problem).
To clear things up:
I'm running the latest versions of BurpSuite and FireFox.
I have installed and reinstalled the BurpSuite certificate using this guide.
I've tried all of this on my iMac, MacBook and iPhone all of these devices yield the same issue
Here bellow is the error message I'm getting:
Here are my BurpSuite Proxy setting:
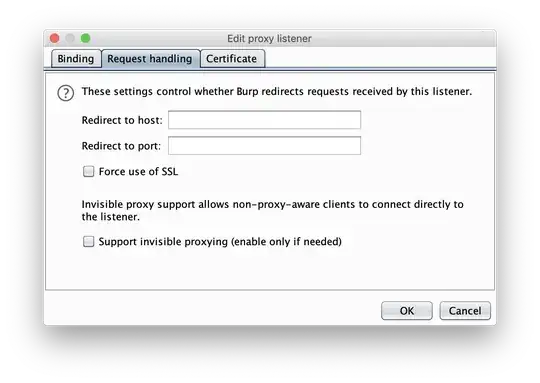
(in the Certificate tab I just have Generate CA-signed per-host certificates selected)
I have been using BurpSuite for over 2 years now and it's the first time I'm facing such an issue, any help is appreciated
I have shared my question with the Portswigger support (the team behind BurpSuite) and got the following response:
Hi
Thanks for your message.
We have reproduced the issue in our testing environment.
It looks like Nike.com are performing a fairly sophisticated check to stop automated tool from accessing parts of their site. Please let us know if you need any further assistance.
Cheers
Liam Tai-Hogan
PortSwigger Web Security