Yes, but it's not entirely straight-forward.
I assume you're talking about Windows code-signing. Any .exe file can have a signature embedded in it:
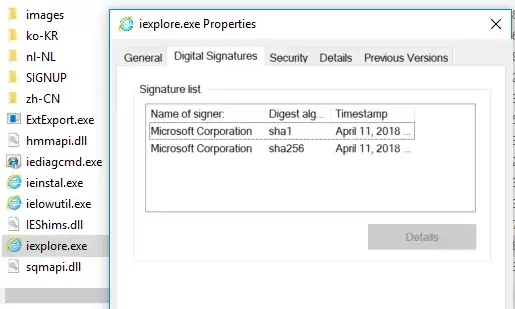
As far as I know, this format only allows a single signature. (though the Microsoft code signing format is very similar to CMS that's used for S/MIME and a few other protocols, so it could in theory carry multiple signatures).
@eckes mentions in comments that you can do detached PGP signatures and present multiple of them. That's ok if you're willing host multiple .sig files next to your software download, and expect users to verify these manually. If you're using standard Microsoft X.509 signatures, then unless I'm missing something, you'll need to provide multiple versions of your binary, each with a signature from a different CA... which seems like it defeats the purpose of proving that it's the same binary.
