Rule name: XSS, HTML Injection - Body
Rule: 100096BHTML
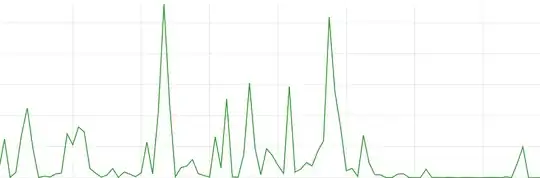
Since about a week ago, requests matching this WAF rule have strongly increased on a customer's website. This is an example graph showing only the number of those flagged requests over 24 hours:
This affects all kinds of targets. Surprisingly for me, especially static files are being requested. Each IP address requests a number of files. The number of files can vary between a few and a few hundred. The set of files requested for each ip address seems to be legitimate.
Sources of the requests are legitimate ip blocks of mobile phone providers and home internet providers of the main targeted countries of the website.
I wonder, how I can deal with this:
- It is not entirely clear to me what exactly is wrong with these requests. I assume, their body contains things it should not contain.
- If my assumption is correct, I would need to log the request bodies.
- Logging request bodies is critical from a data protection issue (GDPR, etc.).
- It might be false positives, but how can I prove it?