I am domestic user and I am getting attacked regularly by a guy that hates me.
Here is the background story: that guy uses Skype resolvers (tools offered by paid DDoS services) to find out my IP based on my Skype ID. He does that because I have dynamic IP, so whenever I go online and sign in to Skype, he discovers my new IP using the Skype resolver. Now I know I could avoid this by creating a new Skype ID (which I did) or by using a proxy service for Skype (which is not always convenient), but I wonder how I could prevent the attacks if he discovered my IP through other means.
What I know for sure is that he is using 2-3 paid DDoS services, so he's not conducting the attack from his PC. I have 100 Mbps download and upload capabilities, my CPU is a Core i7-920 (2.7 GHz quad-core) and I am using the Jetico Personal Firewall, and I am on Window 7 x64. When I am getting attacked, there is not much bandwidth use, but the CPU gets stressed up to 50-60% and I am not able to access any internet resources (browsing doesn't work, chat clients go offline, etc.) The firewall does its best to reject the attacks (as you can see in the screen shot bellow), it doesn't crash or hang, but it is not enough. My Internet connection is bridged, so he's not attacking a router, all the packets hit my system directly. Either way, I don't think a router could do better.
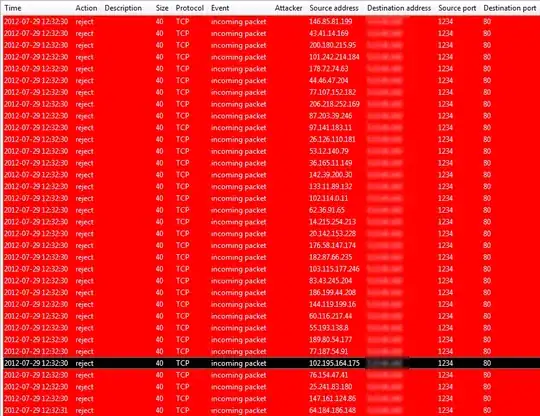
As you can see, all the packets are incoming 40 bytes TCP packets, sent through port 1234 and hitting port 80 on my system (I do not have any service listening on that port, and even if I were, I wouldn't let it be accessed from the outside). I think that the source IPs are spoofed addresses as they come from all over the world. During an attack I get millions of such packets and the only way to stop the attack is by disconnecting from the internet and reconnecting (with a different IP).
My question: is there any way I can protect myself against such an attack without having to disconnect from the Internet and suffer major CPU stressing?