When I attempt git push origin, I get the following error:
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the RSA key sent by the remote host is
SHA256:7zYnlSpxx6z0t477lR5vNYfelxewzWwu8N1X6v+wsZA.
Please contact your system administrator.
Add correct host key in /home/mako/.ssh/known_hosts to get rid of this message.
Offending RSA key in /home/mako/.ssh/known_hosts:1
remove with:
ssh-keygen -f "/home/mako/.ssh/known_hosts" -R "github.com"
RSA host key for github.com has changed and you have requested strict checking.
Host key verification failed.
fatal: Could not read from remote repository.
Please make sure you have the correct access rights
and the repository exists.
This isn't super alarming in itself; it just means the ssh key observed for "github.com" is different this time from the last time I connected.
When I look online to figure out if GitHub has changed their keys lately, I see that their RSA SHA256 fingerprint should be SHA256:nThbg6kXUpJWGl7E1IGOCspRomTxdCARLviKw6E5SY8.
Screenshot in case that page change:
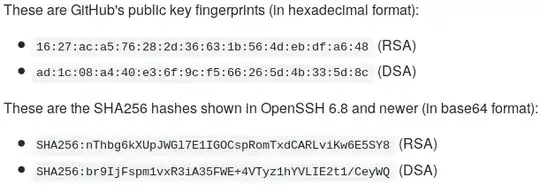
When I run ssh-keygen -l -f ~/.ssh/known_hosts -F github.com I get
# Host github.com found: line 1
github.com RSA SHA256:nThbg6kXUpJWGl7E1IGOCspRomTxdCARLviKw6E5SY8
The fingerprint saved in my known_hosts file matches the one advertised in GitHub's help pages, and does not match the one I observe when I try to push my work.
At this point, should I suppose that something bad is happening? What should I do about it? What further diagnostics should I run?
Update:
On a different network now (my home wifi), and I now I observe the advertised fingerprint. My impression is that this means there's "something wrong" with the wifi at the coffee-shop I was at earlier.
- I'm taking for granted that I shouldn't attempt to bypass the normal ssh protections. If they're really inconvenient I guess I should just use a VPN or my own hotspot?
- Should I treat that wifi network as suspect in other ways? Should I trust that my (https) web is secure?
- Is this a problem that I should ask/expect the business owner to fix?