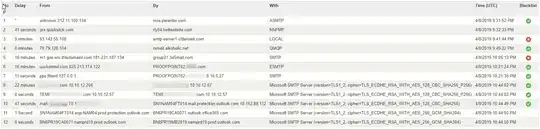
I am trying to figure out how we were spoofed for education purposes. The email came in perfectly with the user's email address and name. The only way we found out was the header information. Most spoofing I see, I can tell by looking at the from address and it will be different but with the person's name. This one was different. In Outlook, it truly looked as if the email was sent from themselves. As you may have guessed they were trying to convince the user that his email was hacked. I have attached an image with the header info. Any help is understanding this would be greatly appreciated as I work on trying to find a way to detect and block.
Asked
Active
Viewed 196 times
2
Bob Waxon
- 23
- 2
-
1Nothing in the information you provide (including the image) really suggests that the mail was spoofed. But this might just be a lack of useful information since you only provide a very limited view into this mail. – Steffen Ullrich Apr 09 '19 at 15:29
-
All I did was remove the companies public IP and domain info. I can't seem to paste the header with the same extractions since it contains to many characters. – Bob Waxon Apr 09 '19 at 15:59
-
Tell me what you need Steffen. – Bob Waxon Apr 09 '19 at 16:02
-
So I couldnt paste my header but I think I was able to make it work in MXtoolbox. Let me know if you can see the header text. It won't be able to process it but who needs that when we know how to read it. – Bob Waxon Apr 09 '19 at 16:50
-
https://mxtoolbox.com/Public/Tools/EmailHeaders.aspx?huid=809dc02c-98c4-4068-b407-a419c08d604a – Bob Waxon Apr 09 '19 at 16:50
-
1The header says that your domain has no spoofing protection, so spoofing is possible. – schroeder Apr 09 '19 at 18:32
1 Answers
0
Authentication-Results spf=none (sender IP is 000.000.000.000)
smtp.mailfrom=uuviummd.com; XXXXXXXXXXXXXXXXX.mail.onmicrosoft.com; dkim=none
(message not signed) header.d=none;XXXXXXXXXXXXXXXXX.mail.onmicrosoft.com;
dmarc=none action=none header.from=XXXXX.com;
The Authentication-Results field of the mail header clearly says that there is neither and SPF policy (spf=none) nor a DMARC policy (dmarc=none) for your domain nor does it contain DKIM records (dkim=none). This makes the domain easy to spoof.
For more on this see Why is it even possible to forge sender header in e-mail?.
Steffen Ullrich
- 184,332
- 29
- 363
- 424