Is there a standard/definitive way to distinguish the end-entity cert in a PKCS#7 (P7B) cert chain? I believe the PKCS#7 standard doesn't not specify sequence when ordering the certs in the chain, but most tools do sequence them in (either bkw or fwd) signing order). And I know an end cert would have different owner/issuer CNs (root's would be the same for both), was wondering if there was a foolproof differentiator say, in the case of an end and intermediate cert, where both would have different owner/issuer (right?). Thx!
Asked
Active
Viewed 285 times
1 Answers
3
CA certificates (V3) always include Basic Constraints certificate extension where isCA attribute is set to True. End-entity certificates either, omit this extension or include extension with isCA attribute set to False. Basic Constraints (RFC 5280 §4.2.1.9) is the most reliable way to differentiate CA and end entity certificates.
Here is an example of Basic Constraints extension for CA certificate in Windows Certificate Viewer:
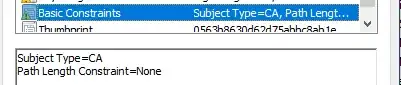
an example of Basic Constraints extension for end entity certificate in Windows Certificate Viewer:
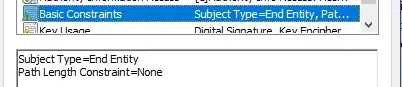
-
Ah, "Basic Constraints" is an X.509v3 extension. And I see I can get at this ext from .Net too; nice, thx! Hmm; what would an intermediate CA signer look like? BTW I assume u meant "...extension for end-entity certificate..." in ur 2nd example. – galaxis Mar 11 '19 at 21:56
-
Intermediate CA signer is CA. – Crypt32 Mar 11 '19 at 21:58
-
Got it. Also friendly reminder to update 2nd example text to reflect "end entity". – galaxis Mar 12 '19 at 21:36
-
Thanks, updated my answer. It was a copy/paste issue. – Crypt32 Mar 12 '19 at 21:42