The Client-Server model in botnets is just the same (with maybe some pimps from botnet family to other) as any client<->server model, its setup like a network with one or more main server(s) that control the transmission of informations from and between each client. As for RATs the botmaster have usually a Command and Control (C&C) server (or servers) in order to orchestrate slaves (clients). This model is called Centralized. While there is also Peer-To-Peer model and Hybrid models
Know:
How does B (the attacker) even know when A (the infected) is online,
if B (the attacker) does not have a server running listening for
connections incoming from infected machines?
While far from being exhaustif, here are some ways described in the following slides:
Internet Relay Chat (IRC)
- Port 6667 or custom port
- join hardcoded channel send
- command/instruction via joined channel (PUSH)
HTTP/HTTPS
- Port 80, 443
- Php based system
- Post request (PULL)
- Snd.php (register the botnet)
- Update.php (update the binary file)
- Stat.php (get the command)
P2P
- UDP
- No fixed port
- Supernode (locate where the C&C server)
There are several maneer to perform this, and keep in mind that usually (if not always) that it's A that notifies B of its presence,whether as a new infection or as an online/offline activity. There is always some kind of Push and Pull methods.
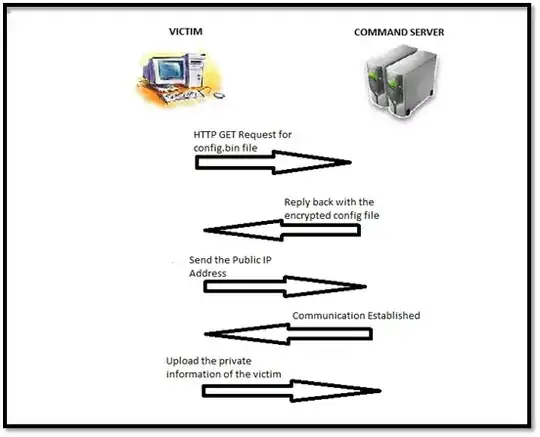
For example once a client of Zeus botnet is infected, he tries to download a config file from the server (B) via HTTP/Getnotifying this way the server of a new infection (called registering):
Some Botnets uses IRC , by setting up some IRC servers, A reports to B and B commands A via IRC commands.
Kraken Botnet for example uses UDP/447 to the C&C server resolved from a fully qualified domain name list.
There is no generic answer, it all depends on the topology/model and how the developers of the botnet in question are smart/skilled.
You can learn more on how botnets communicate from these links. "Detecting Covert Botnets Using Communication Patterns", "Botnet Communication Patterns"
