While others have responded with valid methods such as full-disk encryption. I would not exactly say this prevents disk imaging. Equally, if an adversary has direct access over your machine with unlimited time and money; game over!
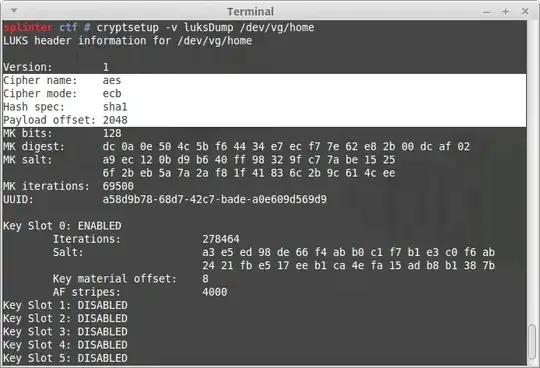
So, cloning the physical disk cannot be prevented using software, but mitigating the chance an adversary will successfully brute-force the master-password with limited resources (time and money) and hence access the decrypted contents can be reduced. If using LUKS consider increasing the number of rounds (iteration count) and key-size. So, we consider the following changes to the default LUKS deployment, remember these changes are done regarding your hardware with respect to your adversaries resources:
Regarding wiping all data on your drive after using LUKS consider overwriting the LUKS header rather than all data as this will be quicker. Arch Linux has fairly extensive documentation regarding overriding the header, but consider using something more extensive like DoD 5220.22-M or Gutmann method for overwriting the necessary portion of the LUKS header. Also, do consider the necessary risks when overwriting data on an SSD.
While some alternative methods could be deployed because the Beaglebone Black uses eMMC memory. They would be classified as secrecy through obscurity which is NOT something we aim for here. So, without deploying something like a TPM, LUKS will be a viable alternative. However, as I understand the LUKS header can be placed on a USB drive. This would allow you to boot the Beaglebone Black, and once decrypted remove the USB drive with the LUKS header and if anyone has physical access to the machine, they would need to extract the decryption keys from RAM (not viable on Beaglebone Black). Otherwise, if the machine is rebooted or powered off, it will be encrypted (as the decryption keys were stored in RAM) and the LUKS header is stored on a USB drive. Hence, nothing can be brute-forced without the USB drive.
