(Something old...) There's this fresh innovation Pretty Good Privacy (PGP). It has been around for almost thirty years and it can sign plain text for both authenticity and integrity. The PGP is known of and widely used for signing email messages, but it has a support for clearsigned text documents. In practice you could sign a message using gpg --clearsign.
Usually gpg --verify is enough for verifying the signature, but --decrypt also prints out the message.
$ gpg --decrypt poc.txt
This is a proof of concept PGP signed text message
for security.stackexchange.com/questions/204285/
gpg: Signature made Tue 26 Feb 2019 03:34:44 PM EET
gpg: using RSA key XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
gpg: Good signature from "Alice <alice@example.com>" [ultimate]
For printed documents the problem is the characters that doesn't show or resembles another character, so there are some limitations. It's not practical to digitize the printout as even a single difference will cause the verification fail. Even a short example message like this is not so simple, as it might have line breaks. Before printing...
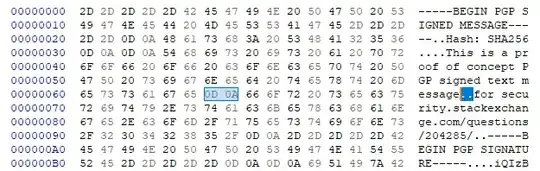
- was there just a new line
0x0A or did it also have a carriage return 0x0D0A,
- was there a space before the new line
0x200A or them both 0x200D0A,
- or was it just a space
0x20 alone and the line break was added during printing.
That's why its better to keep a digital copy even if it's just a plain text message. It's easy to compare the two printouts and verify the digital version of the original. There's no need to verify the modified paper copy.
The PGP signature verifies that you have signed the message as long as you can proof that the key used for signing was yours. On the other hand, the time on the signature can't be trusted as you can fabricate it. You would have to provably publish the signature somewhere. You can publish the signature without the original message as it only contains (SHA256) checksum that is affiliated with your public key. It's a proof that your private key has signed the message in that precise form.
(...something new...) Take a hash of the file, just like in the PGP solution, or even the whole signature, depending on whether you wan't it to be linked to you or not. Put it on a blockchain (e.g. Bitcoin; you can see a lot of them in cryptograffiti.info). Now you have proof of that document existing in that exact form on that specific time, and it'll stay there forever.
As hash algorithms utilizes one-way functions, the hash doesn't reveal the contents of the file. However, anyone having the file can also take the hash and compare it to the one published. Depending on the situation you might want to be associated with the file or not:
You may want to be acknowledged as the creator and prevent someone else from patenting your invention (...something borrowed..).
Or you may have communicated or even leaked something confidential and don't want to have your eye to be the "something blue". These are the tools; use them wisely.
