I just heard a very confused news broadcast about Symantec warning the world about the dangers of formjacking. The newsreader said it involved “hacking the form, not the website” whatever that means.
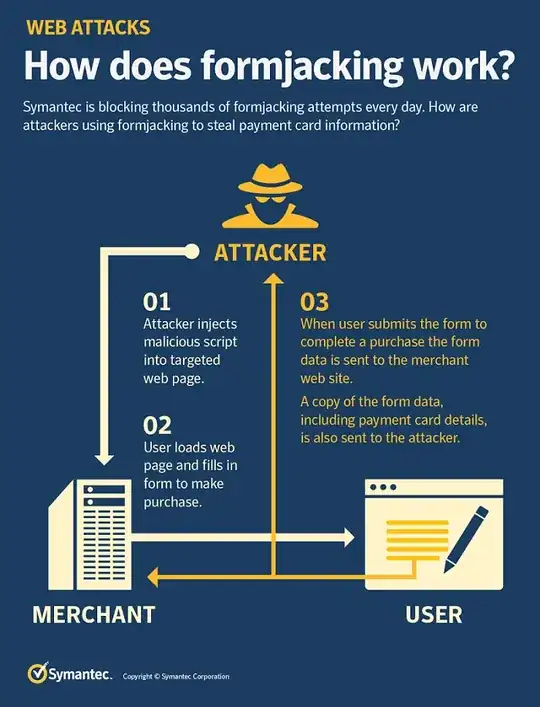
I googled around and found a Symantec blog post about it, where they describe the attack as follows:
- The attacker “injects” malicious JavaScript into the targeted webpage
- The user fills out the form on that webpage
- The JavaScript sends the entered data to the server of the attacker.
However, I would say that if an attacker has write access to the code on the server formjacking is the least of your concerns (and not the actual vulnerability – whatever gave them access is).
Why is formjacking the big deal (it was on the national news where I live) and not the fact that tons of websites (among which British Airways according to Symantec) have a ridiculously large vulnerability that allows attackers access to their servers?