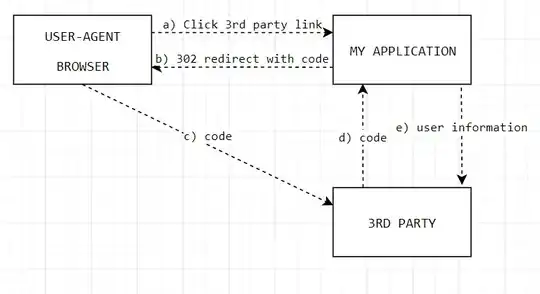
A 3rd party company has requested that we implement single sign-on with them using the below approach. I'm familiar with OAuth grants and OIDC flows but this seems rather odd to me.
The user has already logged into my application when this flow starts.
a) Logged in user clicks a link to access the 3rd party system
b) My application creates a random code against the authenticated user with a time to live of 2 minutes and redirects the user to the 3rd party application with the code.
c) Redirect navigates the browser to the 3rd party application with the code.
d) 3rd party sends the code to my application. My application checks the code was one that was issued earlier and within the allocation time.
e) My application returns user information and the 3rd party treats this as Single Sign-On.
Stuff I'm uncomfortable about...
- Seems to be a poor mans OAuth implementation of the Authorization Code Grant
- No state parameter so there's risk of XSRF
- "3rd party" could be anyone
- Time to live on the code is a bit worrying
- There's no way to expire the user's session in the 3rd Party application. In OAuth, the tokens usually expire after a while.
Is there anything that's obviously bad about this implementation? Do you think I'm potentially overreacting here and this is in fact suitable?