I have a client with a website that sells a book. When someone clicks a button to purchase the book, a form is supposed to pop up (and does). However, I received a screenshot showing that, when that button is clicked, a security warning from Trend Micro also displays see screenshot
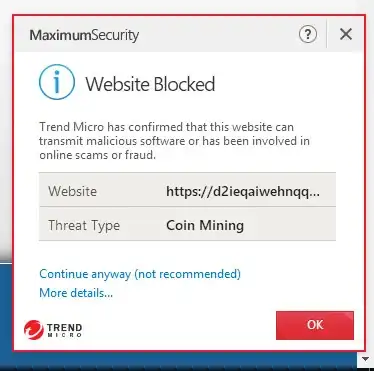 .
.
The URL mentioned in the warning is obviously NOT the same as the website. The website also has valid SSL running on it, too.
I logged into the WordPress Admin and saw no suspicious plugins. I also reached out to GoDaddy (the host) and asked if they could do a server-side scan to find any malicious scripts running, and the person said they found none (though he seemed uninformed regarding this issue).
I'd like to figure out what is triggering this warning as well as how to resolve it and prevent it from happening in the future.
Any ideas?