Note: This question is follow-on from comments on this answer that were broad enough to be a separate question.
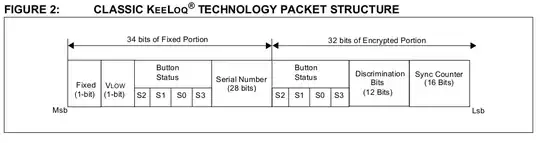
As far as I understand, KeeLoq is a block cipher designed for use in the automotive industry, specifically for keyless entry systems where one master receiver (the car?) needs to be able to register and authenticate transmitters (key fobs) in the field.
Re-quoting manufacturer documentation from the linked answer:
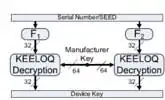
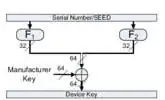
The Normal key generation scheme is the common key generation scheme for KEELOQ technology systems. During Normal Learn, a master key is used (known as the “manufacturer code”). When using the normal learning mechanism, the decoder uses the manufacturer code and the serial number to calculate the decryption key for each transmitter. Using the serial number of each encoder and the manufacturer code, the unique encryption key for each encoder is calculated. The encoder stores only the serial number and the calculated encryption key. The decoder needs to be programmed with this manufacturer code in order to be able to calculate individual encryption keys.
So my question is: how does this cipher work? More specifically:
- How is a derived key calculated from the master key and serial number?
- Serial number of what? Does the receiver need to be told the serial number of each key fob that it is paired with?
- Any other details that make KeeLoq unique and interesting.
I am aware of wikipedia/KeyLoq, but it's a bit of a stub article.