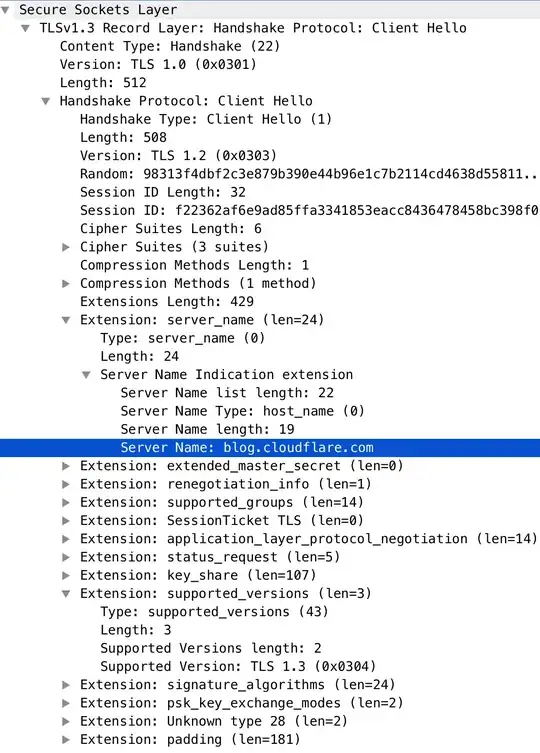
I was just curious about TLS1.3 which Cloudflare is one of the companies leading the implementation. I then visited blog.cloudflare.com and turned on my Wireshark. I am not 100% clear about all technical details of TLS1.3, but one of the new features that I was particularly interested in is Encrypted-SNI, which aims to hide the intended visiting domain name.
I check the pcap, saw both Client Hello and Server Hello as follow:
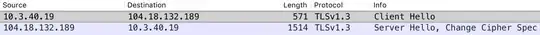
I was surprised to see TLS1.2 was wrapped in the TLS1.3 packet, and the SNI part of TLS1.2 is still there, exposing the server name.
So I wonder whether this is the implementation error or I have been downgraded, or am I missing something? Note that I already configure my Firefox browser to force TLS1.3 only, thus it's not the issue of my browser as you can see in the supported_versions extension.