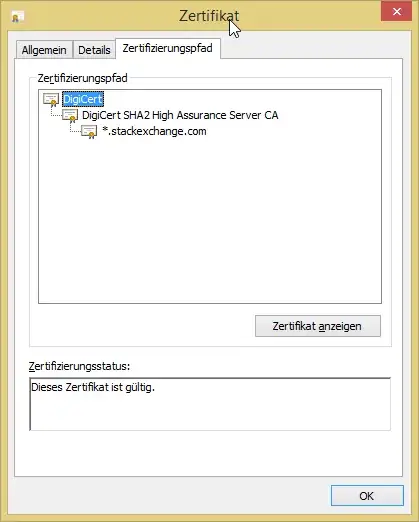
I wanted to find out whether my company can see what I'm posting online as soon as using websites using a valid https certificate.
I know there are a lot of posts here about whether my company can find out which URLs I've visited. Now I wanted to find out whether I'm being intercepted by the proxy-server we use (we have a computer-wide proxy-server in place which is also used for webbrowsing) by means of "faked" https-certificate.
IMHO my company doesn't use such a procedure, but I just wanted to confirm it by some experts on here.
When I'm browser to https://security.stackexchange.com on my companys laptop in firefox, the certificate-hirarchy looks completely identical to the certificate-hirarchy showing in Chrome on my home computer:
Even the certificate fingerprints and serial-numbers are completely the same.
Is my understanding correct that:
- Even though we are using a proxy, it is sufficient to check the certificate hierarchy and when it's the same inside the companys network and in my home network, I can conclude I'm not being sniffed the inputs I do
- The procedure of the proxy-server to "insert" a faked https-certificate, in case there would be such a system in-place, would probably be made system-wide. That means, as I only compared the certificate-hierarchies on a few domains now, it should mean such a procedure will highly likely not be in-place at all, also not for any other domain?
- That means the only way to track my inputs, would be to use some sort of keyloggers? (Which is probably not possible / allowed by law anyhow (living in germany)).
- From what I gathered from the other posts here on stackexchange, they can obviously save from the logs which URLs/hostnames I have visited. They question is: Do they see the full URLs or only the hostname / the target server? Because it could potentially do a big difference whether I visited some reddit page about how to setup some software or some reddit page about po*rn :D Obviously I won't visit these, just frmo a technical POV I want to know what's possible here.
Thanks in advance!