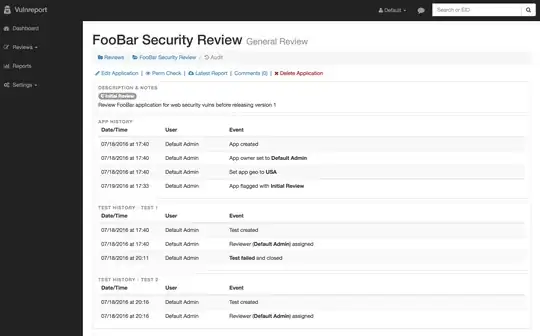
How does your company track the vulnerability management information that happens between receiving a vulnerability scan report and remediating a vulnerability?
Given the following example:
Scan A detects
Vuln 1
Vuln 2
Vuln 3
You decide not to remediate Vuln 2 and 3, but you do remediate Vuln 1. At a later date you conduct another scan (Scan B):
Scan B detects
Vuln 2
Vuln 3
Vuln 4
Putting the vulnerability information into a large master spreadsheet along with remediation decisions (whether or not to remediate) and manually updating it would allow you to keep track of vulnerability decisions so you're not constantly re-evaluating the same vulnerabilities (Vuln 2 and 3 in the example above) from scan to scan.
Is it common practice to have a large master spreadsheet that contains the relevant information for vulnerabilities found by scans (target, vulnerability, risk ranking, remediation decisioning notes, etc...) that is manually kept up to date across vulnerability scans or is there some other common practice or well-known tool(s) that does a better job tracking this information?