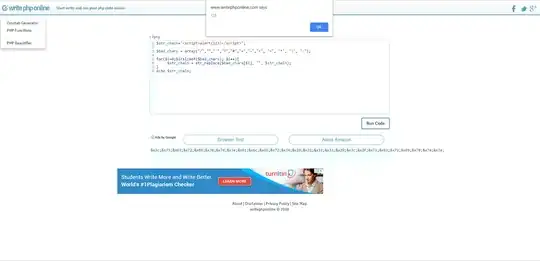
I need to write PHP code in an application in which I have access to the code, because it is a white box.
However, I noticed that they use the following function:
function stripbadchars($str_chain){
$bad_chars = array("/","\\","\"","'","?","#","+","~","<", ">", "*", "|", ":");
for($i=0;$i<sizeof($bad_chars); $i++){
$str_chain = str_replace($bad_chars[$i], "", $str_chain);
}
return $str_chain;
}
When I write in a field of the <?php application, this one, comments to me in the following way: <--?php
And it gives it to me as html. Any way I could do a bypass?