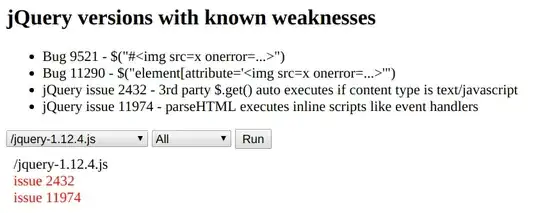
Is this code vulnerable to DOM based XSS?
The application is using jQuery 1.12.4 and i noticed that Data is read from window.location.hash and passed to $() via the following statements:
var target_ = window.location.hash.substr(1);
$('html, body').animate({
scrollTop: $("." + target_).offset().top - $(".site-header").outerHeight()
}, 1000);
What payload could I use to trigger an alert box or execute any JS code? Is this code vulnerable or 100% safe?