I've just learned the theory behind XSS attacks and now I would like to test my knowledge in a legal way.
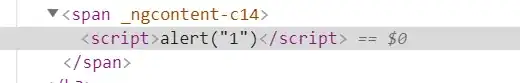
I wanted to "hack" OWASP Juice shop by following steps from this book section "Perform a reflected XSS attack". When I use iframe src="javascript:alert(1)"> as a XSS payload it works as expected (I get alert 1). But when I change it to <script>alert(1)</script> nothing happens, no alert is displayed.
I checked using Chrome Developer tools that payload was injected to the DOM but for some reason script was not executed. Do you have any idea why? Any idea how can I inject more sophisticated payload to OWASP Juice shop?